Sun Aug 11
Cisco Switch Type 7 Passwords and Configuration Recovery
Reversing Type 7 Passwords to plain text and dumping Configuration files straight from a Cisco Switch's filesystem without logging in within a matter of minutes.
Notice
The information provided in this post is intended for educational purposes only. The topics discussed are meant to enhance understanding and knowledge in the field of cybersecurity and network administration.
Unauthorized use of these techniques for malicious purposes is illegal and unethical. I do not condone or support any illegal activities. You are advised to use this information responsibly and within the bounds of the law.
Cisco Switch Type 7 Passwords and Configuration Recovery
I recently bought two Cisco Catalyst 2960-X series switches online that were used and “pulled from a working environment”. Upon receiving the switches, I plugged a RJ45 to USB serial console cable into one of the switch’s console port and attached it to my computer and booted the switch. After all of the switch’s built in tests were completed, I noticed that the switch was configured for TACACS+ authentication and was attempting to resolve a .edu domain name for NTP. The switch also had a label on the front “finearts48sw01” which matches the hostname I saw in the console output after booting.
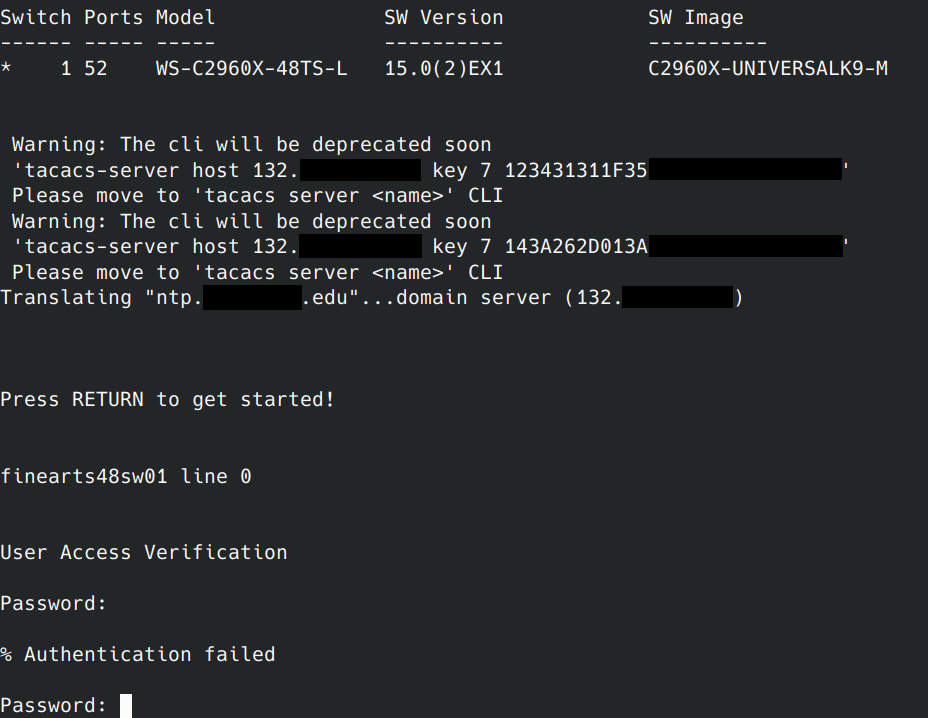
I immediately knew that the switches configuration was not purged and it still had all of the information stored on it. I suppose the seller was right about “pulled from a working environment”.
I tried all of the default passwords I could try and did not have any luck gaining access to a CLI session. Instead of trying to brute force the password, I was going to retrieve it from the configuration file since I had physical access to the switch.
Gaining access to the filesystem and configuration
Because I was locked out of the switch, I could not gain access to a console session to erase the startup configuration.
To gain access to the filesystem, I removed power from the switch and reapplied the power while holding the “MODE” button to the right of the “Cisco” logo on the front plate. This interrupts the boot process of the switch.
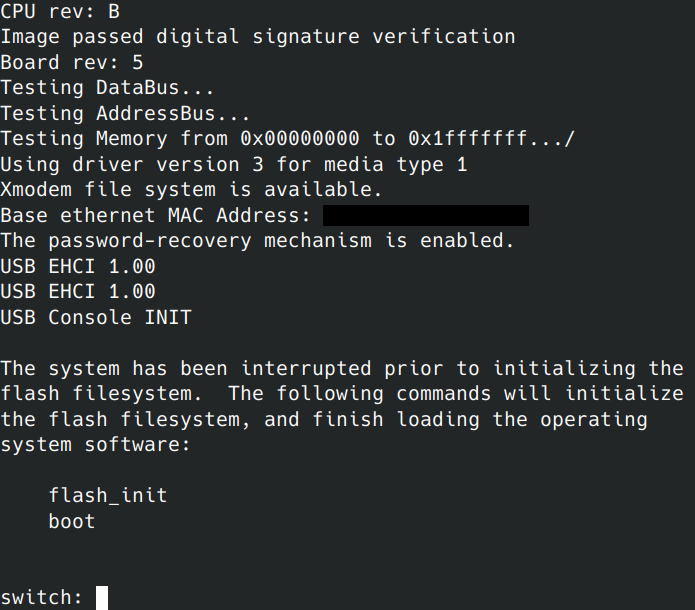
You can initialize the flash filesystem by running:
flash_init
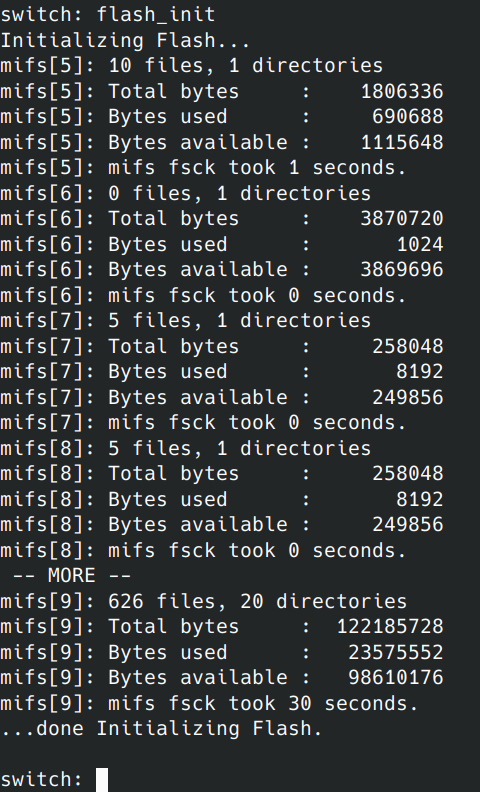
Once the flash is fully initialized and the filesystem is mounted to the system, you can list out the contents of what is on the flash memory by running:
dir flash:
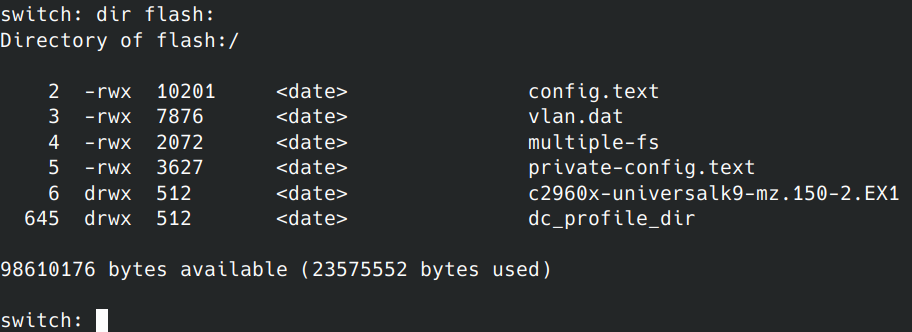
You can cat out the entire plain text configuration by running:
cat flash:/config.text
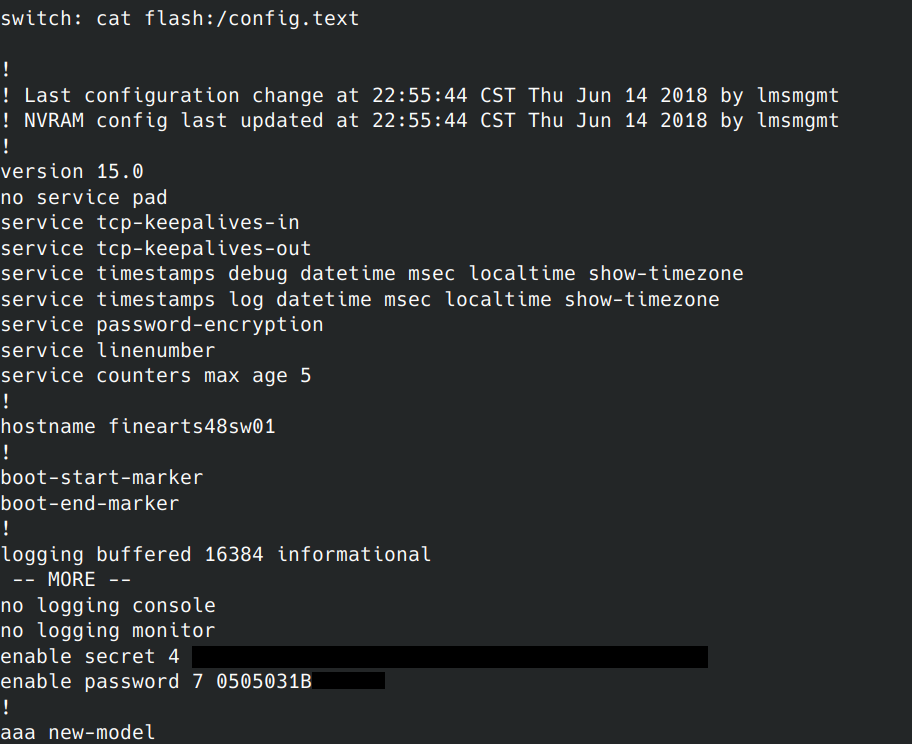
At this point, you have recovered the configuration of the switch.
In this instance, I was able to see hashed passwords (type 7), SNMP strings, the IP addresses of the TACACS+/SNMP/NTP servers used, VLAN definitions, etc. This configuration file contained a lot of internal information about the education institution’s internal infrastructure.
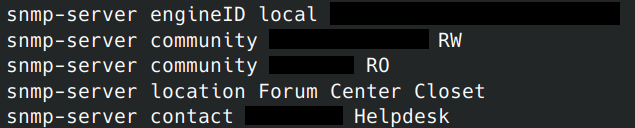
I was also able to see where the switch physically lived before it was removed from it’s environment:
Password Recovery
Passwords are contained in this configuration file. Cisco switches allow you to hash/encrypt the passwords. In this instance, passwords were “Type 7” which is NOT advised to use. See NSA’s document published here.
I’ve copied the table from the document and added a description row to explain what type of password algorithm is used:
| Password Type | Ability to crack | Vulnerability severity | NSA recommendation | Description |
|---|---|---|---|---|
| Type 0 | Immediate | Critical | Do not use | Plain text |
| Type 4 | Easy | Critical | Do not use | SHA-256 Hash |
| Type 5 | Medium | Medium | Not NIST approved, use only when Types 6, 8, and 9 are not available | Salted MD5 Hash |
| Type 6 | Difficult | Low | Use only when reversible encryption is needed, or when Type 8 is not available | Reversible 128-bit AES encryption |
| Type 7 | Immediate | Critical | Do not use | Vigenère cipher |
| Type 8 | Difficult | Low | Recommended | PBKDF2 with SHA-256, 80-bit salt and 20,000 iterations |
| Type 9 | Difficult | Low | Not NIST approved | SCRYPT with 80-bit salt and 16,384 iterations |
Types 8 and 9 are commonly used today. Type 9 is typically considered more secure because it is a Memory-Hard Function (MHF). This means that an attacker attempting to reverse the password would need a substantial amount of memory to brute-force it. In contrast, PBKDF2 (Type 8) does not implement MHF and does not require a substantial amount of memory to brute-force; rather, it can be accomplished with high-powered CPUs, GPUs, and ASICs.
The enable password in this configuration lives towards the top of the configuration file. It starts with “enable password” followed by the type of password followed by the password hash.
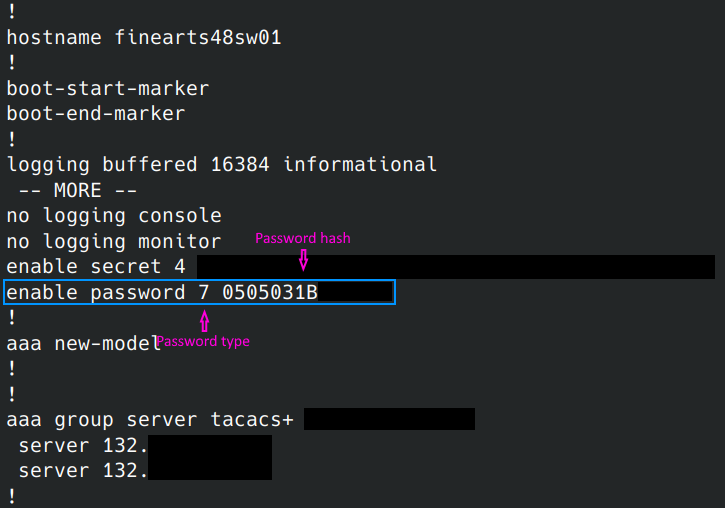
Since this is a Type 7 password, recovery of it is going to be extremely easy.
There are plenty of open source tools that you can use to reverse this Type 7 password.
I will be using cisco7decrypt.py as it can be locally run on the machine with no dependencies. You can find this tool on a GitHub Gist here.
A copy of the source code follows:
#!/usr/bin/env python3
"""
Based on the documentation from:
- http://pen-testing.sans.org/resources/papers/gcih/cisco-ios-type-7-password-vulnerability-100566
- http://wiki.nil.com/Deobfuscating_Cisco_IOS_Passwords
translation = [
0x64, 0x73, 0x66, 0x64, 0x3b, 0x6b, 0x66, 0x6f, 0x41, 0x2c, 0x2e,
0x69, 0x79, 0x65, 0x77, 0x72, 0x6b, 0x6c, 0x64, 0x4a, 0x4b, 0x44,
0x48, 0x53, 0x55, 0x42, 0x73, 0x67, 0x76, 0x63, 0x61, 0x36, 0x39,
0x38, 0x33, 0x34, 0x6e, 0x63, 0x78, 0x76, 0x39, 0x38, 0x37, 0x33,
0x32, 0x35, 0x34, 0x6b, 0x3b, 0x66, 0x67, 0x38, 0x37
]
"""
import argparse
translation = [
hex(ord(char)) for char in 'dsfd;kfoA,.iyewrkldJKDHSUBsgvca69834ncxv9873254k;fg87'
]
def hexadecimal(text):
return int(text, 16)
def decrypt(text):
password = ''
jump, text = int(text[:2]), text[2:]
for i in range(0, len(text), 2):
password += chr(hexadecimal(text[i:i+2]) ^ hexadecimal(translation[jump]))
jump += 1 % len(translation)
return password
def argument_parser():
parser = argparse.ArgumentParser(description='A simple utility to decrypt cisco Type 7 passwords')
parser.add_argument('text', nargs='+', help='the encrypted password that you want to decrypt')
parser.add_argument('-l', '--long-output', action='store_true', help='show a message with the encrypted and decrypted password')
return parser
def main():
args = argument_parser().parse_args()
for text in args.text:
if args.long_output:
print('{}::{}'.format(text, decrypt(text)))
else:
print(decrypt(text))
if __name__ == '__main__':
main()
Using the tool is as simple as passing the hash into it:
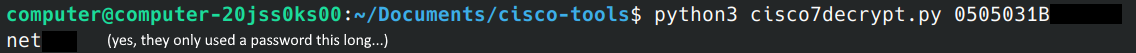
It will spit out a plain text version of Type 7 passwords. This can be used for any Type 7 password in the configuration file.
Testing the recovered password
We can now finish booting the switch after dumping the configuration file and reversing the password to a plain text format. You can run the following to continue the boot process from the boot loader CLI:
boot
Once the switch is booted, press enter and try the decrypted password:
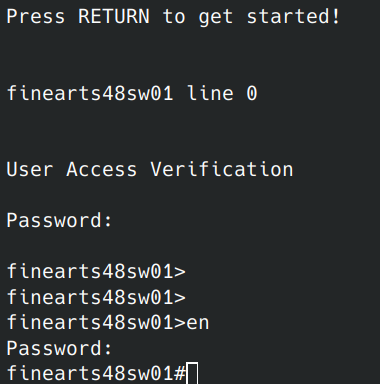
And just like that, we are in…
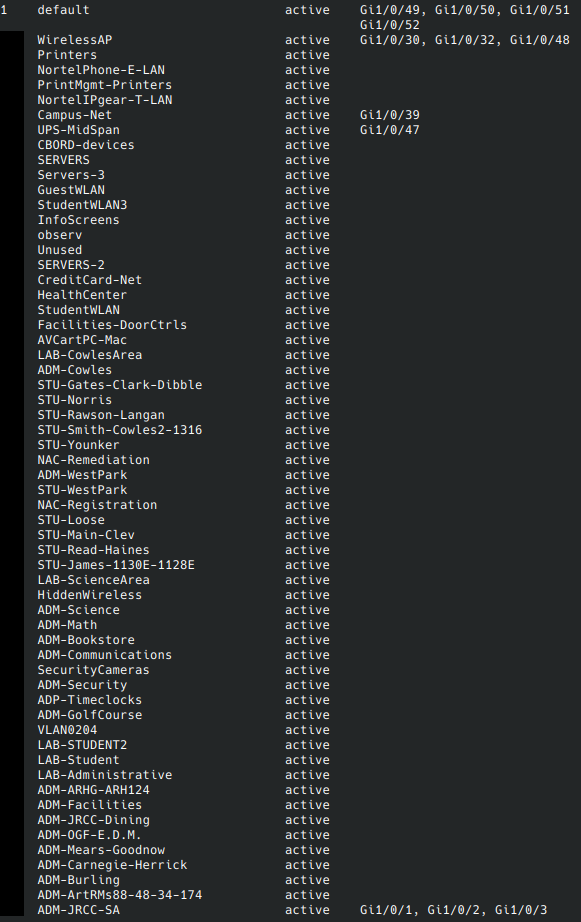
I was able to dump out the VLAN configuration of the switch too.
Here is a partial snip of the VLAN configuration (VLAN numbers removed to protect the educational institution’s security):
Erasing the configuration
Obviously, I am not supposed to have access to this configuration. A report has been made to the education institution about this incident but no response has been received (this happened over a year ago).
I have purged the configuration and the rest of the VLAN database on the switch.
Conclusion
This post should outline the importance of data security when decommissioning old networking equipment and the process of recovering a Type 7 password/configuration from a Cisco Catalyst switch.